
Fortune 500 companies aren’t the only ones flocking to cloud services like Microsoft Azure. Increasingly, hackers working on behalf of the Chinese government are also hosting their tools in the cloud, and that’s keeping people in Redmond busy.
Earlier this year, members of the Microsoft Threat Intelligence Center suspended 18 Azure Active Directory applications after determining they were part of a sprawling command-and-control network. Besides the cloud-hosted applications, the members of the hacking group Microsoft calls Gadolinium also stored ill-gotten data in a Microsoft OneDrive account and used the account to execute various parts of the campaign.
Microsoft, Amazon, and other cloud providers have long touted the speed, flexibility, and scale that comes from renting computing resources as needed rather than using dedicated servers in-house. Hackers seem to be realizing the same benefits. The shift to the cloud can be especially easy thanks to free trial services and one-time payment accounts, which allow hackers to quickly get up and running without having to have an established relationship or even a valid payment card on file.
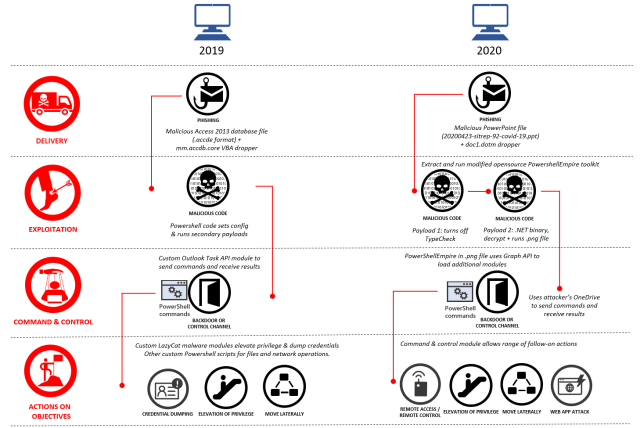
At the same time, Gadolinium has embraced another trend found in organized hacking circles—the move away from custom malware and the increased use of open source tools, such as PowerShell. Because the tools are so widely used for benign and legitimate tasks, their malicious use is much harder to detect. Rather than rely on custom software for controlling infected devices, Gadolinium has recently begun using a modified version of the open source PowerShell Empire post-exploitation framework.
In a post published on Thursday, Microsoft Threat Intelligence Center members Ben Koehl and Joe Hannon wrote:
Historically, GADOLINIUM used custom-crafted malware families that analysts can identify and defend against. In response, over the last year GADOLINIUM has begun to modify portions of its toolchain to use open-source toolkits to obfuscate their activity and make it more difficult for analysts to track. Because cloud services frequently offer a free trial or one-time payment (PayGo) account offerings, malicious actors have found ways to take advantage of these legitimate business offerings. By establishing free or PayGo accounts, they can use cloud-based technology to create a malicious infrastructure that can be established quickly then taken down before detection or given up at little cost.
Gandolinium’s PowerShell Empire toolkit lets the attack group seamlessly load new modules using Microsoft programming interfaces. It also allows attacker-controlled OneDrive accounts to execute commands and receive the results sent between attacker and victim systems.
“The use of this PowerShell Empire module is particularly challenging for traditional SOC monitoring to identify,” the researchers wrote, referring to the systems operation centers where security teams monitor customer networks for signs of cyberattacks. “The attacker uses an Azure Active Directory application to configure a victim endpoint with the permissions needed to exfiltrate data to the attacker’s own Microsoft OneDrive storage.”
Agility and scale work both ways
But while the cloud provides attackers benefits to the attackers, those benefits work both ways. Because the attacks were delivered using spear-phishing emails containing malicious attachments, they were detected, blocked, and logged by Microsoft Defender. And eventually, they were linked back to infrastructure hosted in Azure.
“As these attacks were detected, Microsoft took proactive steps to prevent attackers from using our cloud infrastructure to execute their attacks and suspended 18 Azure Active Directory applications that we determined to be part of their malicious command & control infrastructure,” Thursday’s post continued. “This action helped transparently protect our customers without requiring additional work on their end.”
Microsoft said it also took down a GitHub account Gadolinium used in similar attacks in 2018.
Microsoft is now releasing digital signatures and profile names known to have been used by Gadolinium. People and organizations can use them to tell if they or customers were victims or intended victims of any hacking by the group.
“Gadolinium will no doubt evolve [its] tactics in pursuit of its objectives,” the post concluded. “As those threats target Microsoft customers, we will continue to build detections and implement protections to defend against them.”
"used" - Google News
September 25, 2020 at 05:45PM
https://ift.tt/3mS4ics
Microsoft boots apps used by China-sponsored hackers out of Azure - Ars Technica
"used" - Google News
https://ift.tt/2ypoNIZ
https://ift.tt/3aVpWFD
Bagikan Berita Ini














0 Response to "Microsoft boots apps used by China-sponsored hackers out of Azure - Ars Technica"
Post a Comment